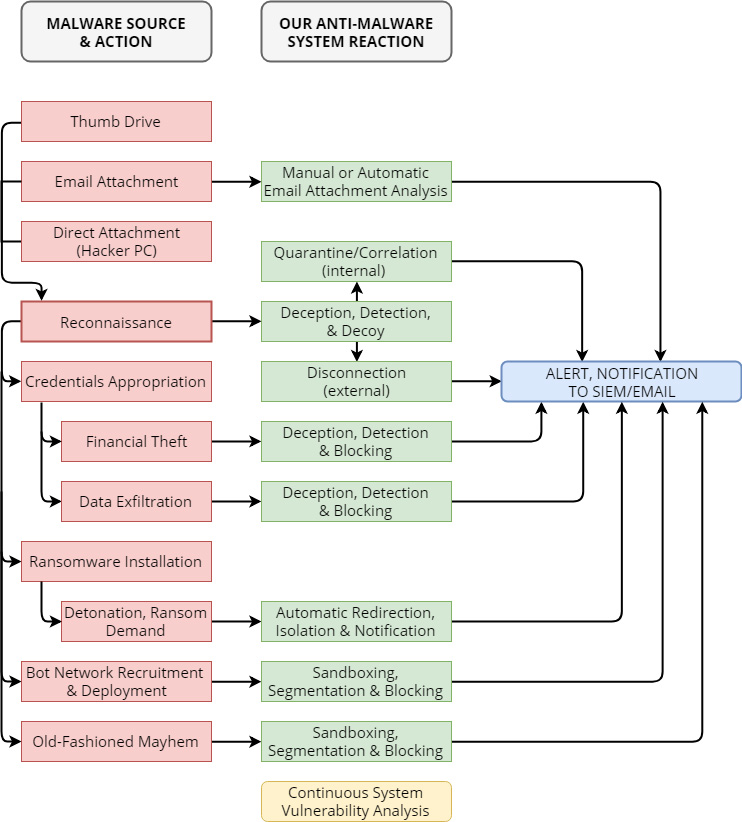
The system creates a set of vulnerable servers, workstations or controllers that look like exploitable resources to any hacker doing reconnaissance. These instances can be configured to look like public-facing servers, internal servers, SCADA controllers, PC-based controllers, infusion pumps, monitors, or regular workstations. When the hacker engages with one of these fake instances the system traps the hacker into a relationship and learns its IP address, an IP address that the hacker is sending information to or receiving external control from, what kind of exploit it is, and what signatures it presents.